The discovery of vulnerabilities in digital products is something that happens quite frequently. As a rule, companies rush to release the necessary corrections for reasons of security, but also of public image. Even though there are more than 60,000 vulnerable NAS, D-Link will not release a fix for the flaw found in its equipment.
Taking into account the information available in the NIST vulnerability database, we can easily see that this flaw in D-Link products is something serious. Searching for CVE-2024-10914, It is described that this is a vulnerability that affects several D-Link models:
- DNS-320 Version 1.00
- DNS-320LW Version 1.01.0914.2012
- DNS-325 Version 1.01, Version 1.02
- DNS-340L Version 1.08

These equipment are typically used in SMEs. The severity level of the vulnerability is 9.2being classified as criticismaccording to CVSS 4.0:
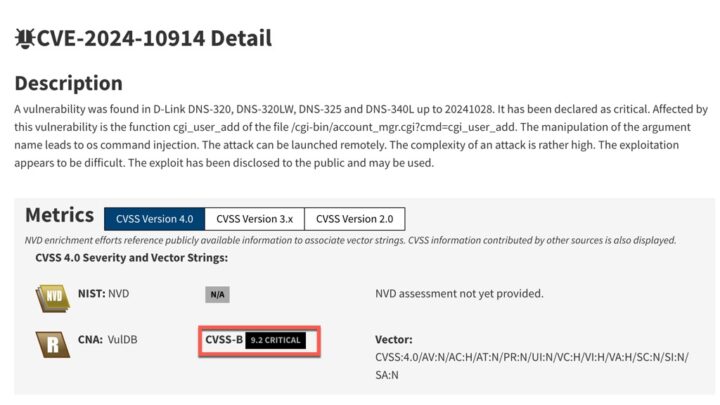
How dangerous is the D-Link vulnerability CVE-2024-10914?
As mentioned, equipment that has this vulnerability is susceptible to attacks via http. The problem lies in the function cgi_user_add, more specifically in /cgi-bin/account_mgr.cgi?cmd=cgi_user_add. Manipulating the name argument allows commands to be sent to the equipment, allowing the attacker, for example, to add users and then have full control of the equipment.
curl "http://(Target-IP)/cgi-bin/account_mgr.cgi cmd=cgi_user_add&name=%27;
;%27"
A search on the FOFA platform returned 61147 results, 41097 of which are unique IPs of vulnerable D-Link devices with the CVE-2024-10914 vulnerability.
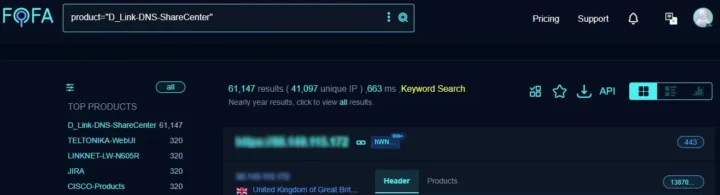
D-Link confirmed here which will not launch any type of update, recommending replacing them with newer devices.
Source: pplware.sapo.pt


